This post will show you how to create a Power BI Embedded Workspace Collection via the new Azure CLI 2.0. People typically create Workspace Collections via the Azure Portal, but that requires clicks and take more time than just doing it in the command line.
IMPORTANT: You cannot get the Power BI Embedded Access Keys using this method. I’m working with the CLI team to get that implemented soon. In the mean-time, you have to go to the portal to get the Access Keys.
1. Install Python
You need Python to install azure-cli via pip.
1. Install Python 2.7 from here:
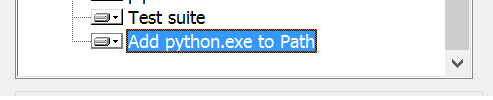
2. Make sure you choose to include Python in your PATH:
2. Install Azure CLI
1. Open a command prompt and execute the following:
pip install --user azure-cli
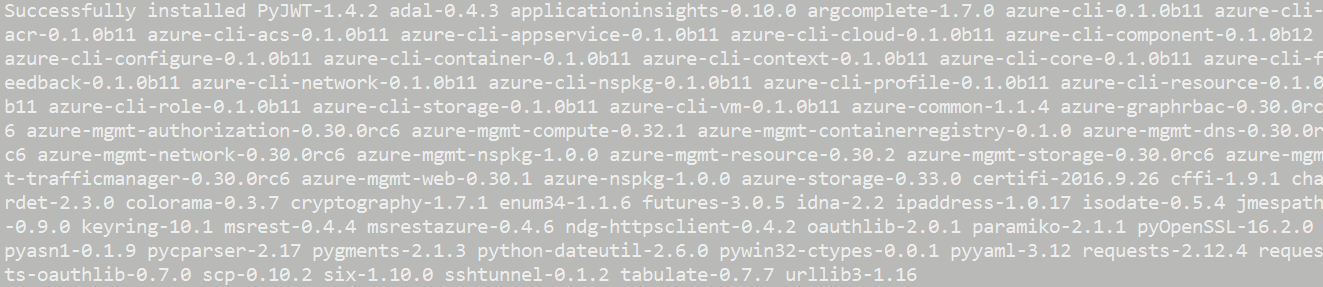
You will see this when it is finished:
3. Add Python Scripts to PATH
1. Find a path similar to this one: C:\Users[user]\AppData\Roaming\Python\Scripts add it to your environment PATH variable. I say ‘similar’ because it might be under ‘AppData’ local or under the versioned Python folder inside of ‘Roaming’
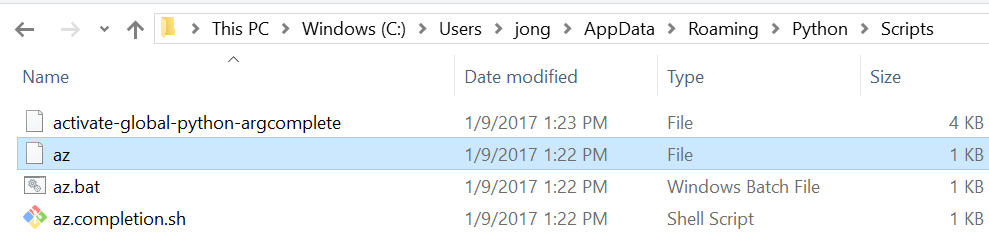
You will see the following when you open that path in Windows Explorer. Notice “az”. If you don’t see that, then the pip install didn’t work.
4. Test az
1. Close all your command prompts, open a new one and run the following:
az
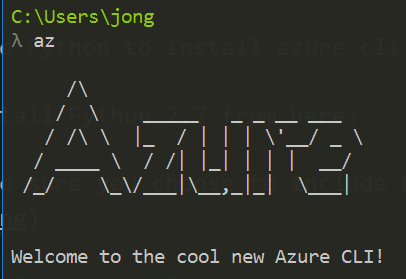
You will see the following output:
5. Login to Azure
1. Run the following command to login:
az login
You will see a message like the following:
To sign in, use a web browser to open the page https://aka.ms/devicelogin and enter the code BVVHR4DRF to authenticate.
2. Go to that URL, enter that code, login with the same account that is assigned to your Azure subscription and then come back to the command prompt. You will see your Azure Subscription metadata in JSON format.
6. Set Current Subscription
This will make sure the Power BI Embedded Resource is created in the right subscription. It sets the subscription as the “current” subscription to any further command will be executed against that subscription.
1. Run the following command to set the current subscription
Replace {subscription id} with your Azure subscription id
az account set --subscription {subscription id}
2. Run the following command to test if the current subscription is correct:
az account show
7. Create an Azure Resource Group
You can either create a new one or use an existing one. If you want to use an existing one skip to the next step.
1. To create a new Resource Group, execute the following command.
Replace ‘westus’ with your desired location and replace ‘jong-rg1’ with your desired Resource Group name.
az group create -l westus -n jong-rg1
8. Deploy Power BI Workspace Collection to Azure Resource Group
Now we want to deploy a new instance of a Power BI Workspace Collection to the Resource group we just created.
You have two options below, with both options you need to:
Replace jong-rg1 with your resource group name
Replace jong-pbie-1 with your desired Power BI Collection Workspace name.
Replace westus with your desired location.
Option 1: Use this Command Line Script
Download this pbie.cmd file I created and run this command. It’s just a wrapper around option 2 below.
pbie jong-rg1 jongpbie-1 westus
Option 2: Execute the Command Directly
az group deployment create -g jong-rg1 --template-uri https://gist.githubusercontent.com/jongio/b55a0f3e8433a0484a6d07f2c7a724ac/raw/789df146e23c7a9c6e56cbec6335991491510b5a/pbiearm.json --parameters "{\"name\": {\"value\": \"jongpbie-test2\"}, \"location\": {\"value\": \"westus\"}}" --debug
You will see the following output - which means your Power BI Embedded Workspace Collection has been created.
See my How to Embed and Filter a Power BI Report with the new Power BI Embedded JavaScript API blog post for instructions on how to create Power BI Workspaces within this Workspace Collection.
Long running operation 'Starting group deployment create' completed with result {'properties': <azure.mgmt.resource.resources.models.deployment_properties_extended.DeploymentPropertiesExtended object at 0x05C6A370>, 'id': u'/subscriptions/[subid]/resourceGroups/jong-rg1/providers/Microsoft.Resources/deployments/pbiearm', 'name': u'pbiearm'}
Application event 'Application.TransformResults' with event data {'event_data': {'result': {'properties': {'template': None, 'parameters': {'name': {'type': u'String', 'value': u'jong-pbie1'}, 'location': {'type': u'String', 'value': u'westus'}}, 'providers': [{'resourceTypes': [{'resourceType': u'workspaceCollections', 'aliases': None, 'apiVersions': None, 'properties': None, 'locations': [u'westus']}], 'namespace': u'Microsoft.PowerBI', 'id': None, 'registrationState': None}], 'timestamp': '2017-01-09T23:01:39.766163+00:00', 'templateLink': {'contentVersion': u'1.0.0.0', 'uri': u'https://gist.githubusercontent.com/jongio/b55a0f3e8433a0484a6d07f2c7a724ac/raw/789df146e23c7a9c6e56cbec6335991491510b5a/pbiearm.json'}, 'parametersLink': None, 'debugSetting': None, 'mode': 'Incremental', 'dependencies': [], 'outputs': None, 'correlationId': u'ebd106fa-d8e8-405a-9ae0-a8d203269575', 'provisioningState': u'Succeeded'}, 'name': u'pbiearm', 'id': u'/subscriptions/[subid]/resourceGroups/jong-rg1/providers/Microsoft.Resources/deployments/pbiearm'}}}
Application event 'Application.FilterResults' with event data {'event_data': {'result': {'resourceGroup': u'jong-rg1', 'properties': {'template': None, 'parameters': {'name': {'type': u'String', 'value': u'jong-pbie1'}, 'location': {'type': u'String', 'value': u'westus'}}, 'providers': [{'resourceTypes': [{'resourceType': u'workspaceCollections', 'aliases': None, 'apiVersions': None, 'properties': None, 'locations': [u'westus']}], 'namespace': u'Microsoft.PowerBI', 'id': None, 'registrationState': None}], 'timestamp': '2017-01-09T23:01:39.766163+00:00', 'templateLink': {'contentVersion': u'1.0.0.0', 'uri': u'https://gist.githubusercontent.com/jongio/b55a0f3e8433a0484a6d07f2c7a724ac/raw/789df146e23c7a9c6e56cbec6335991491510b5a/pbiearm.json'}, 'parametersLink': None, 'debugSetting': None, 'mode': 'Incremental', 'dependencies': [], 'outputs': None, 'correlationId': u'ebd106fa-d8e8-405a-9ae0-a8d203269575', 'provisioningState': u'Succeeded'}, 'name': u'pbiearm', 'id': u'/subscriptions/[subid]/resourceGroups/jong-rg1/providers/Microsoft.Resources/deployments/pbiearm'}}}
{
"id": "/subscriptions/[subid]/resourceGroups/jong-rg1/providers/Microsoft.Resources/deployments/pbiearm",
"name": "pbiearm",
"properties": {
"correlationId": "ebd106fa-d8e8-405a-9ae0-a8d203269575",
"debugSetting": null,
"dependencies": [],
"mode": "Incremental",
"outputs": null,
"parameters": {
"location": {
"type": "String",
"value": "westus"
},
"name": {
"type": "String",
"value": "jong-pbie1"
}
},
"parametersLink": null,
"providers": [
{
"id": null,
"namespace": "Microsoft.PowerBI",
"registrationState": null,
"resourceTypes": [
{
"aliases": null,
"apiVersions": null,
"locations": [
"westus"
],
"properties": null,
"resourceType": "workspaceCollections"
}
]
}
],
"provisioningState": "Succeeded",
"template": null,
"templateLink": {
"contentVersion": "1.0.0.0",
"uri": "https://gist.githubusercontent.com/jongio/b55a0f3e8433a0484a6d07f2c7a724ac/raw/789df146e23c7a9c6e56cbec6335991491510b5a/pbiearm.json"
},
"timestamp": "2017-01-09T23:01:39.766163+00:00"
},
"resourceGroup": "jong-rg1"
}
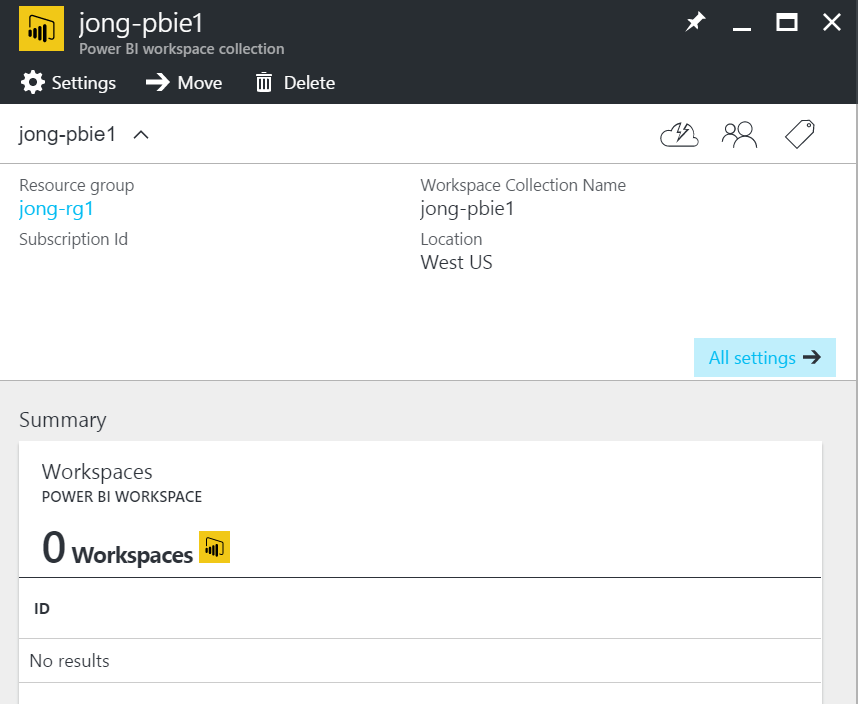
IMPORTANT: You cannot get the Power BI Embedded Access Keys using this method. I’m working with the CLI team to get that implemented soon. In the mean-time, you have to go to the portal to get the Access Keys.